All are aware of the history of breaches from resorts to Hospitals. Even banks are affected by cybercrime, which knows no physical boundaries. Not going a decade ago, let’s talk about 2023- A year in which financial data breaches destroyed records and undermined global trust. The biggest hack, which impacted Bank of America's clients, happened at NCB Management Services, a debt-collecting firm.
Nearly 495,000 people's financial and personal information was compromised in this security breach, discovered by 5 controls of Penetration testing.
Pen testing or security pen testing is a form of ethical hacking in which “white hat” penetration testers mimic the same attack process to test a system’s defenses. It helps to identify exploitable issues and to test the robustness of an organization’s security policies, regulatory compliance, and ability to identify and respond to security issues as they occur.
But the biggest question is: What makes penetration testing effective? The answer lies in the five primary controls of penetration testing, their effectiveness, and practical application.
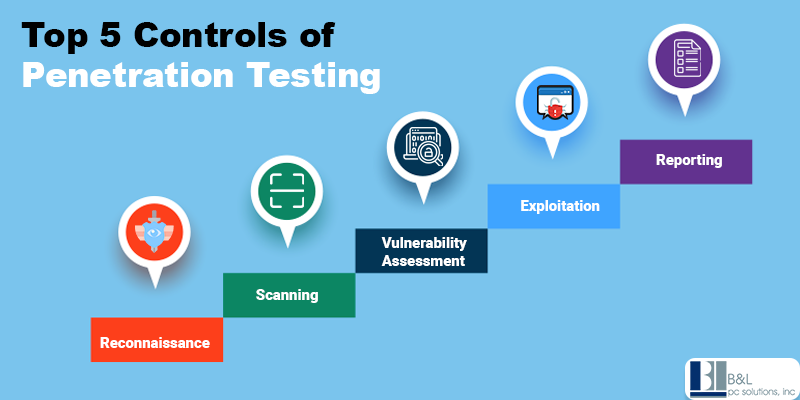
Top 5 Controls of Penetration Testing
The five phases of penetration testing are:
1. Reconnaissance: Gathering information about the target system
2. Scanning: Identifying vulnerabilities using scanning tools
3. Exploitation: Attempting to breach the system
4. Maintaining access: Testing persistence and privilege escalation
5. Reporting: Documenting findings and suggesting fixes
1. Reconnaissance- A Research Phase
A research phase is crucial to gather all the information about the system assets, architecture, and network configurations. Pentesters look for entry points and public-facing services that attackers might focus on. Consequently, a roadmap to find potential vulnerabilities is a start to secure data and save millions.
This targeted testing stage involves two techniques based on the research method: Active Reconnaissance and Passive Reconnaissance. Active Reconnaissance, as the name indicates, involves directly probing the target system to get reliable information using tools like Nmap to detect open ports and other services.
On the other hand, Passive Reconnaissance gains information from publicly available sources like DNS records, social media, company websites, and more. Use both techniques to obtain a comprehensive understanding of the target's weaknesses.
2. Scanning- An Identification Phase
Following the completion of the research, the scanning phase is necessary to examine the system behavior in real-time systems behavior in real-time. With the help of tools like Nessus, OpenVAS, or Acunetix, pen-testers detect open ports and insecure configurations and check network traffic on the target system. It’s important to identify open ports as potential entry points for attackers, and this is beneficial for the next penetration testing phase.
Static and dynamic analysis techniques are used by pen-testers to find possible risks. Dynamic analysis involves testing live systems to dig deep into runtime issues. On the other hand, static analysis consists of reviewing code and configurations without executing them initially.
Once this process is completed and a potential threat is identified automatically, the next step is to involve the pen testers to determine the access level for the hackers to reach their full potential.
3. Vulnerability Assessment- The Interpretation Phase
This mid-penetration phase is dedicated to vulnerability assessment. Now, pen testers are ready to utilize all the valuable information gathered in the above two phases to identify potential vulnerabilities and determine their extent of exploitation.
Pen-testers evaluate the risk of discovered vulnerabilities using resources like the Open Sourced Vulnerability Database (OSVDB) and the National Vulnerability Database (NVD).
However, since the US government built, maintains, and controls this repository of vulnerability management data, NVD is the most commonly used. It investigates software vulnerabilities in the Common Vulnerabilities and Exposures (CVE) database.
The NVD employs the Common Vulnerability Scoring System (CVSS) to assess the severity of known vulnerabilities. This phase performs manual evaluations to confirm findings and identify missed problems. By the conclusion of this phase, your company will have a high-priority list of vulnerabilities, which will direct you to the exploitation phase.
4. Exploitation- The Mimic Attack Phase
Penetration testers can go on to the exploitation stage once all vulnerabilities have been found. This is one of the most important phases, in which pen-testers attempt to breach the system by simulating a real-world assault with tools such as Metasploit and evaluating the impact of a successful breach.
This is the most delicate penetration testing phase because evading security constraints while gaining access to the target system is challenging. Testers also need to make sure the system isn't down or corrupted.
Some standard techniques are accessing databases via SQL injection, Cross-site scripting (XSS), and breaching web programs. This phase provides complete insights into how attackers breach the system and the extent of damage they cause. It also reveals the effectiveness of existing defenses like firewalls or intrusion detection systems.
5. Reporting-The Final Phase
Let’s document the penetration test’s findings in a report to convert useful technical insights into actionable steps to improve the organization’s security health. The most advanced reports include detailed vulnerability descriptions, real-world impact assessments for each identified issue, and remediation strategies for future improvements.
Keep this as a roadmap for strengthening security measures so that the organization will be safe from future data branches and can save millions of dollars.
Read More : What is all About Continuous Penetration Testing and its Benefits?
The Bottom Line
Penetration testing is a cornerstone of modern cybersecurity strategies for securing your startup’s first network or large business and refining your security protocols. Organizations and companies can build robust defenses against threats with perfect penetration tests. Continuous penetration testing identifies vulnerabilities, blocks holes, and ensures cyber controls. This also seeks out vulnerabilities in infrastructure and applications to develop constant, continuous controls that can keep up with the ever-evolving cyber threat era.
Now is the time to contact BLPC, an IT Support Company Long Island to eliminate cyberattacks, as we follow every step with utmost security. Use our penetration test to safeguard your data and yourself. Our penetration testing services will demonstrate how easily hackers can access your data and develop a strategy to ensure your staff practices excellent cyber hygiene. Get your first free penetration test.
Frequently Asked Questions
1. What are the three types of pen testing?
Pentesting types are based on the practices followed: black-box, white-box, and gray-box testing. All these types present the pentester with different facets of information.
2. What is a full penetration test?
Pentesting or Penetration testing is a security practice where pen-testers attempt to find and exploit vulnerabilities in applications, software, or more. Complete penetration testing aims to check an organization’s weak spots regarding security, which attackers can take control of and exploit our data.
3. Is Pentesting similar to QA?
Pentesting is a security-oriented process that uses coding structures to detect loopholes, while QA only checks for processes that follow the complete process while detecting vulnerabilities.
4. How much time it will take to complete penetration testing?
Penetration testing is a long-term process that provides full-fledged security and can take anywhere from one to 15 weeks, depending on the size of the company, complexity, budget, technology, and more.
Tags: 5 Controls of Penetration Testing, 5 phases of penetration testing