Rising threats require protecting personal and commercial data. Cybersecurity is just as crucial to companies holding their clients' sensitive information as to Internet users. Cybersecurity services Long Island safeguards the computer, its network, and its data against intrusions, threats, or hacking incidents.
Sadly, cyberspace threats have advanced and sophisticated levels today, and there is a higher need for excellent quality cyberspace security among users, especially in companies situated in high-risk areas like Long Island.
This blog explains its importance and how cybersecurity specialists can help.
What is CyberSecurity?
At its most fundamental understanding, cybersecurity refers to safeguarding computers, computer networks, and information systems from being attacked by malicious entities. These may take several forms: technical, such as viruses, Trojans, worms, phishing, etc, and social engineering approaches, among many others.
All these types are designed for personal identity compromise, stagnating the company's operations, or achieving unlawful access to confidential information.
Indeed, anyone who purchases goods and services, pays bills, works, dates, or communicates with friends over the Internet can understand why security in the cyber world is such an essential aspect.
Cybercrime mainly uses phishing. That is sending fake emails or messages masquerading as well-known organizations to scam people into giving away sensitive information. Cybersecurity consultant Long Island can help protect people's systems from hackers who wish to get personal benefits or maybe vandalize the systems.
Types of CyberSecurity Threats
In the virtual world, various risks have a potential threat to the company or personal information. Common cyber attacks include.
Malware
Malware comprises viruses, worms, Trojan horses, and spyware. Their primary focus is to infect and damage devices and systems. A malware infection may cause a device to become unusable, or a hacker may extract confidential information from the victim without their awareness.
Phishing
Phishing is a type of crime in cyberspace that attempts to acquire sensitive data such as user names, passwords, and credit cards through fraudulent emails or websites linked to that email.
Ransomware
Ransomware is an attack in which a user's files are locked, and money is demanded to obtain the key to the data. It's on the upsurge, and criminal activities aim at just about every kind of business, regardless of their scale.
Social Engineering
These techniques can be used to gather information from individuals by appealing to their character traits. Social engineering can easily bypass standard technological security systems by misleading people into disclosing passwords or other credentials.
Types of Cybersecurity Solutions and Their Key Functions
Here’s a table that outlines the types of cybersecurity solutions and their key functions:
| Cybersecurity Solution | Description | Key Function |
|---|---|---|
| Firewall Protection | A security system to watch and control network traffic flow in and out. | Blocks unauthorized access while allowing legitimate communication. |
| Antivirus/Antimalware | Software designed to detect and remove malicious software such as viruses, worms, and trojans. | Scans and eliminates harmful software to protect systems. |
| Encryption | Encoding data to prevent unauthorized access. | Makes data unreadable for unauthorized users; ensures safety of sensitive information |
| Intrusion Detection Systems (IDS) | Monitors network traffic for suspicious activity or known threats. | Detects and alerts on potential security breaches or attacks. |
| Data Backup and Recovery | Solutions that automatically back up data and facilitate recovery in case of loss. | Ensures data integrity and restores operations after a breach or system failure. |
| Multi-factor Authentication (MFA) | Requires multiple forms of identification before granting access to systems. | Adds an extra layer of security by verifying identity with more than one method. |
| Vulnerability Management | Tools designed to identify, assess, and fix vulnerabilities in software and networks. | Identifies weaknesses in systems and provides solutions to patch them. |
| Security Information and Event Management (SIEM) | Cumulative and analytical security data across an organization. | Monitors real-time activities and provides insights into potential security risks. |
| Endpoint Protection | Secures devices (such as computers, smartphones, and tablets) that connect to a network. | Monitors and protects endpoints from malware and cyberattacks. |
| Threat Intelligence | Solutions that collect and analyze information about potential or active threats. | Helps businesses stay ahead of evolving threats and plan appropriate defenses. |
Why Does Cybersecurity Matters?
Cybersecurity is becoming increasingly critical. Anyone using the Internet for business or personal reasons exposes themselves to risks. Anyone can clone your identity, withdraw funds from your accounts, blackmail you, or even destroy your company's reputation.
The risks are much worse for businesses. Cybercrime steals companies' money and information and reveals business-related continuities. More than the loss of profits associated with a breach is the legal implication, loss of customer trust, and long-term damage to the company's reputation. Research also shows that a data breach costs millions for any organization.
Other essential aspects where cybersecurity plays a role are identity theft and privacy concerning social security numbers, health information, and payment card information. The leakage of such data puts businesses at high risk of identity theft, fraud, and other expensive losses.
Cybersecurity as a Service for Business
Hence, investing in multi-layered cybersecurity solutions is no longer discretionary for companies but has become mandatory. The tech specialists of a cybersecurity service providerLong Island can best identify the risks and protect the network, keeping the data safe by constant monitoring.
Small and medium enterprises generally require more financial and workforce resources to set up an internal IT security department. Here lies the actual difference a cybersecurity consultant will make in your business.
Security consultants offer professional services to firms where they develop a strategy for security requirements necessary in specific organizations. The professional could provide everything from network protection to preparing a plan for acting if there's a cyber-attack. Thus, exciting and practical cooperation with an expert counselor helps strengthen defense mechanisms in the company and prevent risks even if they grow to a catastrophic scale.
Beating Cyber Threats in Business—Call Our Cybersecurity Team Now!
How can a Cybersecurity Expert Protect You?
A cyber security consultant Long Island is an expert who has been trained in security, especially in identifying such gaps. Such experts are investigators. They detect possible threats of breaching an organization and then protect it through programs like firewalls, encryption, and intrusion detection systems. Cyber security goes beyond just protecting; it ensures systems are impenetrable, minimizing the chances of a breach.
Daily duties range from constant risk analysis. It denotes identifying liability areas within a given system concerning vulnerabilities that cybercrime can penetrate. Upon observation, professionals enforce features such as patching, passwords, and secondary forms of identification to enhance security.
Besides, cybersecurity consultants may invest their time in training employees on proper measures, like spotting phishing scams or protecting data. Therefore, it becomes essential for a firm to have a cybersecurity expert who can combat cyber threats and protect the smooth operations of the business.
Key Facts of Cybersecurity: Recent Years
To focus more on the necessity of cybersecurity, take a look at some of these scary stats:
Statistics note a 38 percent rise in cyber attacks against businesses in 2023. Small companies were said to be the most targeted since they often lacked proper protection measures.
Cyber threats affect one out of five small businesses, and 60% fail within six months due to loss of finance and operations. Global cybersecurity spending will reach over $200 billion by 2025, with companies and governments increasing spending above levels to keep up with growing threats.
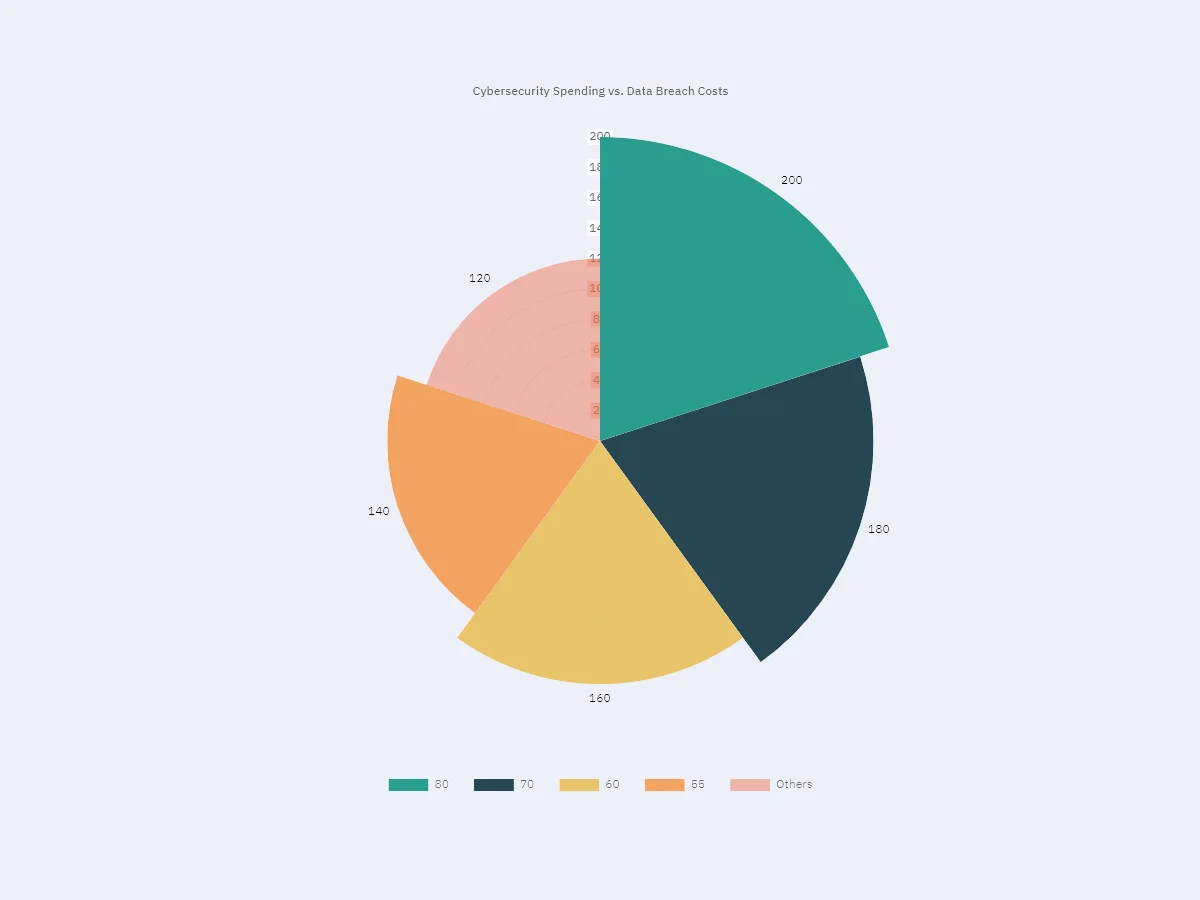
Here is a bar chart comparing the costs of data breaches with investment in cybersecurity in the last years:
| Year | Cybersecurity Spending ($ Billion) | Data Breach Costs ($ Billion) |
|---|---|---|
| 2020 | 120 | 50 |
| 2021 | 140 | 55 |
| 2022 | 160 | 60 |
| 2023 | 180 | 70 |
| 2024 (Projected) | 200 | 80 |
More concretely, the chart shows that more companies are aware of the considerable costs of cyber threats, which correspondingly increase cybersecurity spending. Analyzing the data trends reveals a clear connection between increased cybersecurity spending and lower costs associated with breaches.
Read More Blog : 5 Ways To Implement Cybersecurity Strategy In Your Business
FAQs
1. How do I know that my business should adopt cybersecurity services?
If your business experiences critical system slowdowns, phishing emails, unauthorized access, or sharp changes in network behavior, you will require cybersecurity services.
2. How do people stop committing cyber crimes?
In their attempt to avoid becoming victims of cyber crimes, people ought to be sure to use strong passwords and most authentication methods, update software, and shun suspicious links or downloads.
3. At what point should a business change its security strategies?
Suggested best practices for cybersecurity should include an assessment at least twice a year or soon after significant changes have been implemented. Updates ensure businesses protect themselves against new threats in the market.
4. Is cybersecurity necessary for big companies alone?
An organization has no hiding place from cyber threats, regardless of size. Data protection needs to be secured regardless of the company's size.
Conclusion
Security is essential because competitors try to hack personal and business information from your computer or any connected device. Additionally, it is necessary to adopt preventive measures as cyber threats continually evolve. Whether you are a business or an individual, the most effective strategy is to seek services from cybersecurity experts.
If you still can't decide which direction to take, get hold of a cybersecurity consultant in Long Island. He can make a security plan to help keep you safe from the existing and upcoming threats that cybercriminals will make.
Do not let this be the last hacking nightmare your company has to encounter. Contact our cybersecurity experts now and protect your business from the next threat!
Tags: Cyber Security Consultant Long Island, Cyber Security Services Long Island, Types of Cybersecurity Solutions, Types of CyberSecurity Threats, What is Cybersecurity